NEWS
In Soviet Russia Smartcard Hacks You
The smart card stack is the piece of software on a computer system that interacts with smart cards (aka chip cards) when a card is inserted into a card reader. Imagine breaking into an IT-system by just inserting a manipulated card.
Don’t Hack Smartcards, Use Them for Hacking Computers!
At X41 we are always looking for interesting targets to play with and to test out new attack vectors. Our researcher Eric Sesterhenn started looking into smart card security, since smart cards are associated with a very high level of trust and are often used in the authentication process. Therefore, attacks against a smartcard or the smartcard stack would allow an attacker to get a high privilege level quickly.
A lot of attacks against smart cards have been performed in the past (see https://www.youtube.com/watch?v=62DGIUpscnY) but noch much work has focused on hacking the driver side of the smart card stack. Smartcard drivers present a very interesting target from the attackers point of view since they contain multiple parsers and usually run with high privileges (e.g. root on linux systems).
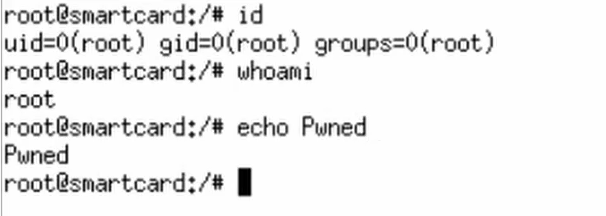
What the Fuzz?
Eric decided to take a look at different open source smart card drivers. Through extending X41’s fuzzing framework he developed several tools in order to identify security issues in the drivers. These tools allow to test the OpenSC smart card stack, and PCSC based drivers on linux as well as Winscard based smartcard drivers on Microsoft operating systems. This helped him uncover several memory corruptions which can be abused to gain code execution on the attacked system by just inserting a malicious smartcard into the attached card-reader. This means the attacker is not only able to login as any user, but instantly as the root-admin.
Furthermore, an issue was uncovered which allows to replay smart card logins in certain cases, which is exactly the kind of attack smartcards should prevent.
For more details watch Erics Talk at defcon or beVX. If you are using open source smartcard drivers make sure to support the projects by donating or supporting the development.
I Want All the Details!
Here you go, let’s start with the facts:
Facts
- Affected smart card stacks are Yubico Piv, OpenSC, libykneomgr and the Apple Smart Card Services project.
- Various vulnerabilities were identified in the different software products. Mostly these are from the following categories: Buffer Overflow, Out of Bounds Memory Reads/Writes and logic bugs.
- Attackers can use manipulated smart cards to exploit these vulnerabilities.
- Possible impacts of successful exploitation are: Code Execution, Crash / Denial of Service, Authentication Bypass in distinct scenarios. Often these services are run with root/administrator privileges.
- The different software vendors/maintainers have been informed and are working on solutions.
- X41 D-Sec is going to publish further details starting 8th of August 2018 and in a DEF CON talk an 11th of August.
Advisories
Here are the detailed advisories:
- Advisory X41-2018-001: Multiple Vulnerabilities in Yubico-Piv
- Advisory X41-2018-002: Multiple Vulnerabilities in OpenSC
- Advisory X41-2018-003: Multiple Vulnerabilities in pam_pkcs11
- Advisory X41-2018-004: Off-by-one zero write in libykneomgr
- Advisory X41-2018-005: Multiple Vulnerabilities in smartcardservices
How Can I Fix / Workaround These Vulnerabilities
X41 worked with the affected vendors to create and release patches that fix the discovered issues. Since a fixed version is not officially available in case of OpenSC yet, X41 decided to make the following repositories including fixes public:
- https://github.com/x41sec/OpenSC
- https://github.com/x41sec/pam_pkcs11
I Want to Know More About This Fuzzing Framework, Can You Check my Software for Bugs?
Sure, can do! Just send us an email with “I want to know more about your fuzzing services!” in it to info@x41-dsec.de and we will provide some extra information to you. You can also ask for the link to the tools used for the smartcard driver fuzzing.